TrustedSec
@TrustedSec
Followers
74,457
Following
792
Media
925
Statuses
4,115
End-to-end Cybersecurity consulting team leading the industry, supporting organizations, and giving back. #Hacktheplanet Blogs, news, webinars, and tools!
Fairlawn, Ohio
Joined November 2011
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
JUNGKOOK
• 687589 Tweets
casilla
• 233596 Tweets
WNBA
• 232617 Tweets
#EleccionesMéxico2024
• 151695 Tweets
Cardi
• 104158 Tweets
Ligue 1
• 69817 Tweets
Querétaro
• 56034 Tweets
Rojo
• 47551 Tweets
Maldives
• 46740 Tweets
Whindersson
• 41479 Tweets
対象の連載作品
• 31619 Tweets
بن نافل
• 30056 Tweets
アニオリ
• 24210 Tweets
Sporting
• 22505 Tweets
Sinner
• 20555 Tweets
Gazzede SoykırımaDurDe
• 20517 Tweets
RIP Rob
• 18007 Tweets
ヒロアカ
• 15888 Tweets
Metz
• 15670 Tweets
Mattarella
• 13055 Tweets
ユメ先輩
• 11551 Tweets
Oviedo
• 10632 Tweets
Angehörigen
• 10424 Tweets
Beileid
• 10306 Tweets
Last Seen Profiles
Pinned Tweet
We are excited to announce that TrustedSec is a Leader in the 2024
@Forrester
Wave™ for Cybersecurity Consulting Services! Find out why we were recognized by downloading the report now:
2
27
69
We have open sourced our legal documentation used for physical penetration tests.
The purpose is to help the community and organizations protect their employees when conducting testing.
Includes three docs:
MSA
SOW
Authorization Letter
#TrustedSec
28
775
2K
We have just released a new tool for exploiting CVE-2019-19781.
Our goal was to keep private as long as possible to have a longer window to fix.
Other researchers have published the exploit code in the wild already. Cats out of the bag.
#TrustedSec
17
464
834
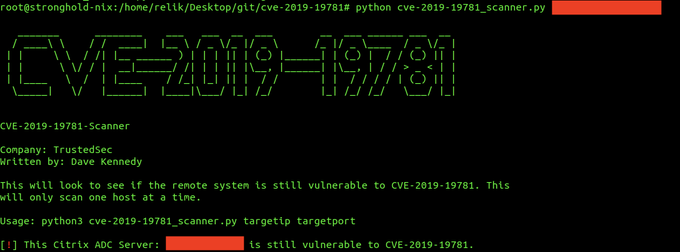
We've just released a scanner that checks to see if a server is vulnerable for CVE-2019-19781.
It does not actually exploit the target and is erfectly safe with no impact on the system.
#TrustedSec
9
320
682
PenTesters Framework (PTF) v2.3 “All the Tools” released.
Adds 7 new tools including rdp scanner, support for internal gitlab, support for customized installs of only certain tools, and more.
(Fixed link)
#TrustedSec
7
231
510
Secret's out!
@Carlos_Perez
announces the release of the TrustedSec
#Sysmon
Community Guide. Discover the vision for making the guide and how you can contribute to making the best
#resource
for all things sysmon!
5
206
447
New Public Tool Release: Hate_Crack
Automated Hash Cracking Techniques with Hashcat
Written by:
@Spoonman1091
#TrustedSec
8
262
396
The PenTesters Framework (PTF) version 2.2 “Tool Haven” released. Adds support for docker containers, number of new tools and fixes. Total of 252 tools now!
#TrustedSec
2
163
376
With initial access to a M365 account, Red Teamers can potentially find a treasure trove of sensitive information.
@Flangvik
goes over three tools (and one script) that he believes to be the modern-day Triforce for initial access. Read it now on our blog!
1
144
376
A message from CEO
@HackingDave
regarding the recent incident at the Dallas County Courthouse Judicial Branch Building in Iowa.
9
181
363
We are proud to announce the addition of
@Carlos_Perez
as lead of the Research and Development team at
#TrustedSec
.
Excited to have you on board Carlos!
Great addition to our team, and our continued commitment of having amazing folks.
39
54
355
For almost a year, invisible password spraying could be performed against any
#Azure
tenant due to a vulnerability in
#MicrosoftGraph
. In our latest blog,
@nyxgeek
walks us through how these attacks could have been carried out. Read it now!
3
153
338
Senior Security Consultant
@Jean_Maes_1994
gives us the first comprehensive resource about all things
#relaying
. This guide covers a range of techniques from most common to the lesser-known.
4
167
335
New version of the PenTesters Framework v2.3.1 “All the Tools” released.
Adds pexpect checks for gitlab support and requirements installation.
#TrustedSec
2
136
305
🚨URGENT🚨 Our
#IncidentResponse
team has put together a playbook of recommended actions to provide some level of assurance that your organization is no longer affected by the SolarWinds backdoor
#solarigate
3
150
296
New tool release from
#TrustedSec
@Ben0xA
+
@Spoonman1091
: “NPS_Payload”
Automated msbuild code exec with NPS.
5
215
288
New Tool: Introducing TrevorC2 - a legitimate user browser and site emulation for command and control.
#TrustedSec
9
179
278
Senior Security Consultant
@Oddvarmoe
gives us a look through the eyes of a
#hacker
using phishing by leveraging Azure Information Protection (AIP) in his latest
#blog
Next Gen Phishing - Leveraging Azure Information Protection - TrustedSec
9
126
265
Our Targeted Operations team recently looked to improve their knowledge management strategy.
@L1NKD34D
provides a behind-the-scenes look at how Obsidian has been customized and evaluated as a solution. Bonus! It's available to as an open-source resource.
11
85
268
Do you wish you had a step by step guide and
#GitHub
resources to deploy infrastructure automation across a
#RedTeam
infrastructure?
@curi0usJack
thought you might. His latest
#blog
"Automating a RedELK Deployment Using Ansible", is a must-use resource❗
0
113
255
New release: Magic Unicorn v3.0 - largest code release in years for Unicorn. Adds custom shellcode and Cobalt Strike support for PowerShell, HTA, and Macro attacks and much much more.
#TrustedSec
4
157
248
Our new
#blog
post by
@mega_spl0it
and
@4ndr3W6S
takes a deep dive into how Active Directory (AD) attribute-based detections can be built and how to identify where an adversary may be hiding. Read the first of this 3-part series now!
0
96
250
#TrustedSec
is expanding its training with online, public offerings!
@HackingDave
shares how these instructor-led courses will help further educate our
#InformationSecurity
community and industry
#TrainingTuesday
1
93
236
Principal Security Consultant
@Oddvarmoe
made an exciting discovery while using password-spraying tools in Microsoft Office 365 during a recent engagement. Read our latest
#blog
to find out how he went from error to entry!
4
66
245
New to security? We have a job for you! Our Associate Security Consultant role will provide training on cutting-edge research, technical-oriented skills, communication skills, and consulting, all in a positive and relaxed workforce environment
#apply
26
111
240
Senior Security Consultant
@nyxgeek
helps you hone your brute-force attacks against O365, and shows you how to extract valuable user lists and group memberships once you have credentials
2
111
239
PenTesters Framework (PTF) v2.3.2 released.
Adds 9 new tools and multiple bug fixes.
#TrustedSec
2
87
233
Magic Unicorn 3.7 released.
Evades second stage detection on meterpreter and stability improvements on powershell obfuscation.
#TrustedSec
0
115
235
PenTesters Framework (PTF) v2.3.4 released.
Defaults to python3 for PTF and TrevorC2.
#TrustedSec
1
94
231
Magic Unicorn 3.2.1 released. Adds better evasion techniques and updates to README.
#TrustedSec
2
100
225
.
@HackingDave
has been busy traveling ✈️so
@SecShoggoth
has stepped up as the "New Office Dave"
#HappyHalloween
10
30
225
PenTesters Framework (PTF) v2.3.5 released. Adds new tool “unlock” for app locker bypasses and a number of enhancements and fixes.
#TrustedSec
2
71
219
In response to the recent
#Citrix
ADC (NetScaler) CVE-2019-19781 Remote Code Execution vulnerability, the TrustedSec IR, offensive, and research teams provide files and locations that may contain evidence of a compromise
3
144
221
The new Cybersecurity Education Program
@BedfordHS
has officially taken off🚀
Take a peek inside our launch event last week and learn more about how this program will impact students!
7
40
214
The Social-Engineer Toolkit v8.0 codename “Maverick” beta released.
New features, enhancements, fixes, and more. Work in progress.
#TrustedSec
3
91
208
Until
@Oddvarmoe
joined the
#RedTeam
he never worked with Cobalt Strike. Read how he (sometimes humorously) did things but learned to be a better Cobalt Strike operator in his journey and you can too!
#infosec
1
81
210
Senior Security Consultant
@oddvarmoe
does a deep-dive on how to find the specific Anti-Virus signature using manual testing and then shows techniques that can be used to bypass them in the first blog post on our ✨spiffy✨ new website!
3
98
208
Consultant Christopher Paschen debuts what may be a new method of
#persistence
that takes advantage of the telemetry found in
#Windows
versions for the last decade
1
111
211
Azure cloud can be compromised even with Domain Admin status. Learn about the dangers of
#Azure
SSO machine account compromise in our new
#blog
by Security Consultant Edwin David.
#CyberSecurity
#PenetrationTesting
0
87
197
PenTesters Framework (PTF) v2.1.3 released. Adds mitm6 and bug fixes on tool dependancies.
#TrustedSec
1
98
194
Happy birthday
@HackingDave
🥳
Leave your favorite
#DaveMoments
here to make his day a little more special 🥰
35
16
190
Ever wanted to exploit that Group Policy modify access you have? Get a crash course on practical
#redteam
GPO client-side extension abuse in this
#security
#blog
from
@curi0usJack
3
98
191
Magic Unicorn 3.2.6 released. Adds obfuscation and evasion techniques for macro and HTA injection methods. Also adds better evasion in PowerShell attack vector.
#TrustedSec
2
80
185
In the first of this
#blog
series,
@rootsecdev
examines the weaponization of token theft. Follow along as he analyzes the behavior of attackers compromising Microsoft 365 users and devices using APT 29 (Midnight Blizzard) tradecraft.
0
50
180
New major release of Unicorn v3.2 - adds three new attack types with the new SettingContent-ms extensions.
Supports MSF, Cobalt Strike, and custom shell code with MSHTA downloader.
#TrustedSec
5
110
176
Every network is different but
@jarsnah12
has noticed a common setting through many
#RedTeam
engagements that allow him to easily inject Rogue DNS records for malicious intent. Read his
#blog
for a full demonstration!
3
87
162
Even for dedicated disciples of
#Mimikatz
, NetSync may be a feature most aren’t familiar with. Senior Security Consultant Andrew Schwartz delves into what it is, how it’s executed, what’s needed to perform the attack, and two possible attack paths
2
82
164
The
#Log4J
vulnerability is as serious as it gets. To help organizations prevent, detect, and mitigate this vulnerability, we’ve put together actionable guidelines and recommendations for how to detect and respond. Updates added when available.
2
68
167
New Release: Magic Unicorn 3.5.1 - adds AMSI_BYPASS mode which uses the technique described here: to disable AMSI as part of the payload in Unicorn. Also added new features (print_decoded and more).
#TrustedSec
0
86
162
New version of Magic Unicorn released v3.6.1.
Slims payload size down substantially, adds better encoding and obfuscation.
Adds ability to use HTA and Macro generation with custom shellcode.
#TrustedSec
1
65
163
Our new "Learning Sysmon" YouTube series has officially launched! 🎉 Research Team Lead
@Carlos_Perez
will serve as your guide through these weekly training videos. Enjoy the first episode "What is Sysmon?" now!
1
56
161
From building payloads, testing evasions, and practicing offensive techniques, a must-have for every seasoned tester is a lab environment.
@W9HAX
walks us through how to deploy a dynamic AD lab environment for attack simulation. Read it now on our blog!
1
43
159
Find out how VBS works alongside driver signature enforcement to protect the Windows kernel, and how
@_xpn_
went about bypassing this to load unsigned drivers.
1
79
156
Don’t get lost in an unknown network!
@Carlos_Perez
is breaking down the problem with Enumeration of Active Domain (AD) in his latest
#blog
From tester to defender, this is important for all
#security
professionals
0
85
157
Exciting news!
We just created a
#TrustedSec
public Slack for anyone to use and interact with the folks here.
Come join our group! We will have frequent updates, code, discussions and more.
Come say hello to the
#TrustedSec
team and get to know us.
6
45
153
'Malware: Linux, Mac, Windows, Oh My!' Our latest post on how to hunt for adversaries on Linux by finding binaries that shouldn't be present along with other ways to maintain access.
#trustedsec
0
77
147
Magic Unicorn v3.8.3 released.
Payload size reduction, signature bypasses, code cleanup and more.
#TrustedSec
0
80
154
Magic Unicorn v3.4 released!
Incorporates better evasion techniques, multiple bug fixes for macro and HTA methods, better handling on randomized variables, improved CS and shellcode checks and much more.
#TrustedSec
3
85
153
Unicorn v3.9 released.
* Incorporates an obfuscated
@_RastaMouse
bypass for AMSI.
* New evasion techniques for getting around detections.
* Splits payloads into different stages for AMSI bypass + Unicorn payload.
#TrustedSec
2
72
152
BLOG: Attacking Self-Hosted Skype for Business/Microsoft Lync Installations
From TS:
@nyxgeek
.
#TrustedSec
3
116
147
IR Lead
@SecShoggoth
starts a 3part
#series
“Adventures of an RDP Honeypot” with an introduction to remote desktop
#security
He’ll detail ways to protect RDP installations and pitfalls when configuring these protections.
#StayTuned
for more!
0
54
148
Founder and CEO
@HackingDave
talks about what it means for TrustedSec to be named a Leader in the The Forrester Wave™ Cybersecurity Consulting Services, Q2 2024. Watch the full video on YouTube!
Download the full report here:
9
28
145
Magic Unicorn 3.8.1 released.
Adds new method for platform detection, obfuscation, and a fix for python2 raw_input when using AMSI bypass.
#TrustedSec
1
75
142
Research Practice Lead
@Carlos_Perez
has created
#SysmonGuide
video tutorials for our
#Sysmon
Community Guide! You can now go to our page or YouTube channel to enjoy these short video tutorials on different topics of this powerful tool
#infosec
0
65
143
Was your system exposed to the
#CVE
-20200688 exploit?
#TrustedSec
shows you how to detect it!
1
74
144
Magic Unicorn v2.8 released. Shortens length of attack and much better obfuscation.
#TrustedSec
1
98
141
Check out our latest post by
@HackingDave
, titled "Weaponizing .SettingContent-ms Extensions for Code Execution" based on awesome research from
@enigma0x3
and
@SpecterOps
. You'll find out how to get code execution from obscure filetypes.
#TrustedSec
2
79
142
In this guide from
@GuhnooPlusLinux
, you'll learn how the new
#BOFLoader
extension allows BOFs to be used from a
#Meterpreter
session. Discover new attacks made possible in Meterpreter and avoid common errors.
0
77
142
Our latest
#blog
post explores the combination of old and new techniques for attackers. In the first of a three-part series, Senior Research Analyst
@freefirex2
walks us through programming
#RPC
calls into
#BOFs
.
2
51
142
TrustedSec Announces New Impede Detection Platform!
Visit our website to learn more from TrustedSec Founder and CEO,
@HackingDave
on how you can unleash the power of advanced detection engineering to enhance your organizations cybersecurity posture!
2
48
139
Limitations on guest user permissions in
#MicrosoftEntra
might not be as restrictive as they appear. In our latest
#blog
,
@nyxgeek
uncovers a method that enables guest accounts to access user and group data — a reminder to change your default settings.
3
50
135
Magic Unicorn v3.2.5 released - adds signature evasion for Defender on Metasploit shellcode (other shellcode is fine and no issue).
#TrustedSec
6
54
136
🚨 Critical
#cybersecurity
vulnerability 🚨
#Microsoft
has taken action against an
#Outlook
vulnerability (CVE-2023-23397) that's been actively exploited for almost a year. Find out how it works and what you can do to mitigate the threat.
2
67
132
Learn how
@jarsnah12
got past an engagement dead end using two underutilizing
#Mimikatz
features in his
#blog
"Azure Account Hijacking using mimikatz's lsadump::setntlm"
0
63
134
We are super excited to announce that we just added
@Oddvarmoe
to the
#TrustedSec
team!!!
Welcome to the red team!
17
10
130